1. A computer is presenting a user with a screen requesting payment before ...
Oct 21, 2020 · A computer is presenting a user with a screen requesting payment before the user data is allowed to be accessed by the same user. What type ...
A computer is presenting a user with a screen requesting payment before the user data is allowed to be accessed by the same user. What type of malware is this?
2. Cybersecurity Essentials Chapter 3 Quiz Questions Answers
May 19, 2022 · A computer is presenting a user with a screen requesting payment before the user data is allowed to be accessed by the same user. What type ...
Cybersecurity Essentials v1.1 Chapter 3 Quiz Questions Answers. Chapter 3: Cybersecurity Threats, Vulnerabilities, and Attacks
3. CyberOps v1.1 Chapter 1 Exam Answers
A computer is presenting a user with a screen requesting payment before the user data is allowed to be accessed by the same user. What type of malware is this?
1. A computer is presenting a user with a screen requesting payment before the user data is allowed to be accessed by the same user. What type of malware is
4. Check Your Understanding > Cybersecurity and the Security ...
Jan 9, 2019 · A computer is presenting a user with a screen requesting payment before the user data is allowed to be accessed by the same user. What type ...
In this sample chapter from CCNA Cybersecurity Operations Companion Guide and the Cisco Networking Academy, you will learn about the who, what, and why of cyberattacks—plus review available resources to prepare for a career in cybersecurity operations.
5. What is Malware? Malware Definition, Types and Protection - Malwarebytes
Malware, or malicious software, is a blanket term for any kind of computer software with malicious intent. Read more below. Think you have malware?
All you need to know about malware. What it is, where it comes from, and how to protect against it. Learn actionable tips to defend yourself from malware.

6. What is Phishing and How Does it Work? | Definition from TechTarget
Attackers commonly use phishing emails to distribute malicious links or attachments that can extract login credentials, account numbers and other personal ...
Learn about the types of phishing, how they work and common phishing techniques. Examine some phishing examples and how to prevent a phishing attack.

7. Ransomware Quiz | Federal Trade Commission
Missing: presenting | Show results with:presenting
Someone in your company gets an email. It looks legitimate — but with one click on a link, or one download of an attachment, everyone is locked out of your network.

8. Chapter 8-Protecting Your System: User Access Security, from ...
User access security refers to the collective procedures by which authorized users access a computer system and unauthorized users are kept from doing so. To ...
Introduction to User Access Security Commonly Asked Questions Policy Issues User Access Security Countermeasures User Access Security Checklist
9. Duo Administration - Policy & Control
This is the default policy for new applications. Allow access without 2FA - Users who are already enrolled in Duo must use two-factor authentication. Users who ...
Duo’s Policy & Control feature enable centralized settings management.

10. Microsoft Privacy Statement
The Microsoft Privacy Statement explains what personal data Microsoft collects and how the company uses it.
11. App Store Review Guidelines - Apple Developer
The App Store Review Guidelines provide guidance and examples across a range of development topics, including user interface design, functionality, content, ...
The App Store Review Guidelines provide guidance and examples across a range of development topics, including user interface design, functionality, content, and the use of specific technologies. These guidelines are designed to help you prepare your apps for the approval process.

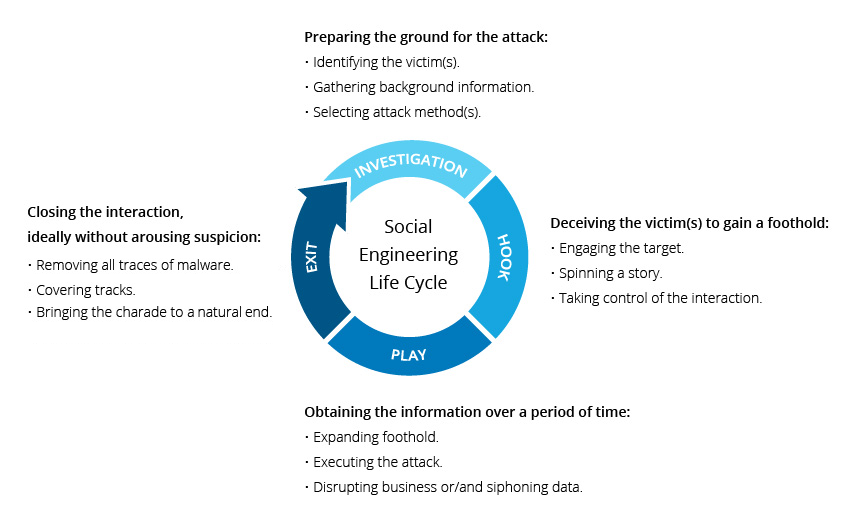
12. What is Social Engineering | Attack Techniques & Prevention Methods
Scareware involves victims being bombarded with false alarms and fictitious threats. Users are deceived to think their system is infected with malware, ...
Social engineering uses psychological manipulation to trick users into making security mistakes or giving away sensitive information
13. What Is Ransomware Attack? Definition, Types, Examples, and ...
Sep 26, 2022 · A ransomware attack is a form of malware attack in which an attacker seizes the user's data, folders, or entire device until a 'ransom' fee is ...
Ransomware attack is defined as a form of malware attack in which an attacker or a cybercriminal locks and encrypts the victim’s data, files, folders, or the entire computer.
